
Evad IT Solutions - Zero Trust Security Solutions create a ring around your IT network and prevent all and any authorized access into your environment. Our end-point ring fencing and whitelisting solutions

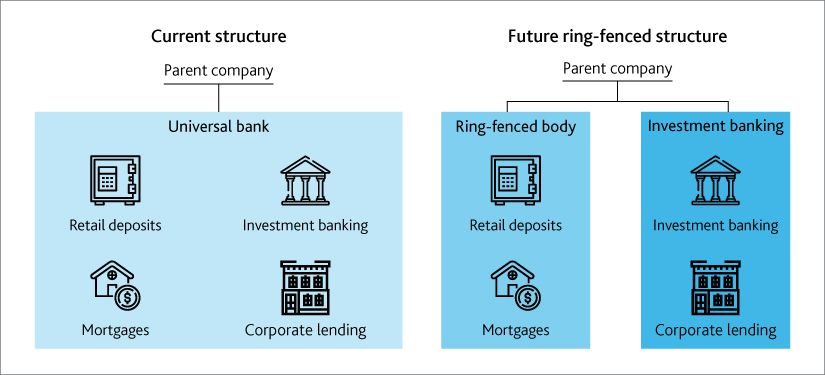
Chapter 11. Bankers without Borders? Implications of Ring-Fencing for European Cross-Border Banks in: A Guide to IMF Stress Testing

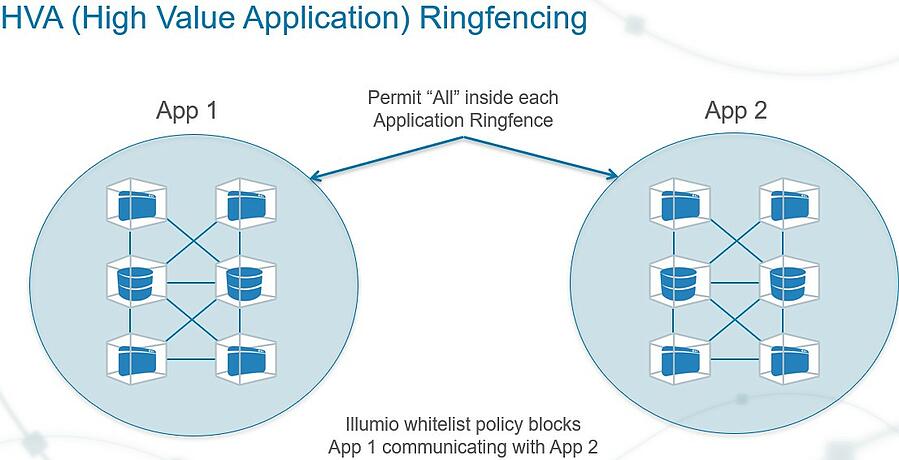
GCC. - GCC through Guardicore technology, called 'Application Ring Fencing', helps security teams to give critical applications the security focus they require by providing a visual map of how they work, making















![PDF] Guide to ring-fencing of local government-run water utilities | Semantic Scholar PDF] Guide to ring-fencing of local government-run water utilities | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4831c329a800e0621a926cd8c36c25619133b846/74-Figure4-1.png)

